Nessus is a vulnerability scanner tool that is used to check security compliance of the hosts.
I’ll be installing Nessus free version i.e. Nessus Essential on Ubuntu VM.
I have installed Ubuntu 22.04 and assigned static IP to it.
Nessus bits are available here
https://www.tenable.com/downloads/nessus?loginAttempted=true
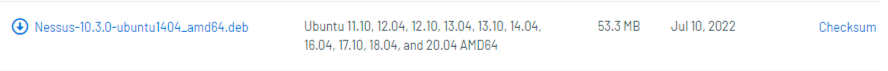
Please download appropriate file as per the OS in you lab. In my case I have used Nessus-10.3.0-ubuntu1404_amd64.deb.
To complete Nessus Installation an Activation code is needed. You can Get activation code from the same link above.
Click on Get Activation Code.

Enter necessary details like Name & Email id to get the activation code. In my case I have selected Nessus Essentials.
To install Nessus copy the bits onto the Ubuntu VM.
root@ubuntu:/home/ubuntu# ls | grep Nessus*
Nessus-10.3.0-ubuntu1404_amd64.deb
root@ubuntu:/home/ubuntu#
Run the installation command
root@ubuntu:/home/ubuntu# apt install -f ./Nessus-10.3.0ubuntu1404_amd64.deb
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
Note, selecting ‘nessus’ instead of ‘./Nessus-10.3.0-ubuntu1404_amd64.deb’
The following NEW packages will be installed:
nessus
0 upgraded, 1 newly installed, 0 to remove and 50 not upgraded.
Need to get 0 B/53.3 MB of archives.
After this operation, 0 B of additional disk space will be used.
Get:1 /home/ubuntu/Nessus-10.3.0-ubuntu1404_amd64.deb nessus amd64
Selecting previously unselected package nessus.
(Reading database … 162782 files and directories currently installed.)
Preparing to unpack …/Nessus-10.3.0-ubuntu1404_amd64.deb …
Unpacking nessus (10.3.0) …
Setting up nessus (10.3.0) …
Unpacking Nessus Scanner Core Components…
Created symlink /etc/systemd/system/nessusd.service → /lib/systemd/system/nessus d.service.
Created symlink /etc/systemd/system/multi-user.target.wants/nessusd.service → /l ib/systemd/system/nessusd.service.
– You can start Nessus Scanner by typing /bin/systemctl start nessusd.service
– Then go to https://ubuntu:8834/ to configure your scanner
root@ubuntu:/home/ubuntu#
Start Nessus Scanner by typing /bin/systemctl start nessusd.service
root@ubuntu:/home/ubuntu# /bin/systemctl start nessusd.service
Check the status of the Nessus service
root@ubuntu:/home/ubuntu# systemctl status nessusd.service
nessusd.service – The Nessus Vulnerability Scanner
Loaded: loaded (/lib/systemd/system/nessusd.service; enabled; vendor prese>
Active: active (running) since Thu 2022-09-08 02:40:43 EDT; 1min 17s ago
Main PID: 136434 (nessus-service)
Tasks: 14 (limit: 1084)
Memory: 66.5M
CPU: 35.330s
CGroup: /system.slice/nessusd.service
├─136434 /opt/nessus/sbin/nessus-service -q
└─136435 nessusd -q
Sep 08 02:40:43 ubuntu systemd[1]: Started The Nessus Vulnerability Scanner.
root@ubuntu:/home/ubuntu#
Go to https://UbuntuVM_IP:8834/ to configure your scanner
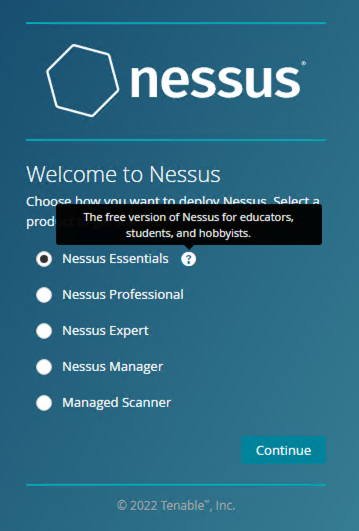
Select Nessus version, in my case it Nessus Essentials. Click Continue.
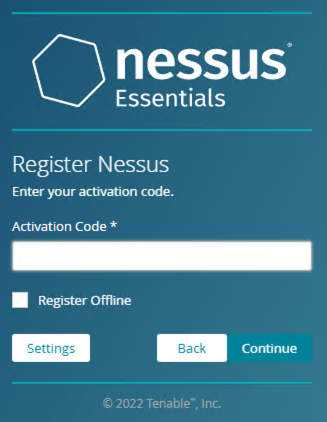
Enter the Activation Code & Click Continue.
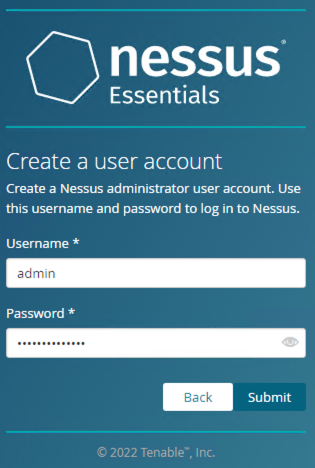
Create administrator user account & Click Submit.

Nessus configuration will continue. Let it complete.
After initialization is complete login into Nessus with the administrator account.
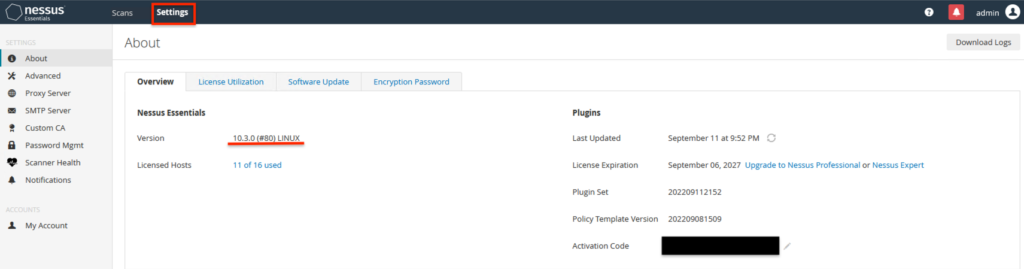
Click on the Settings tab, it’ll give details about the installed version.
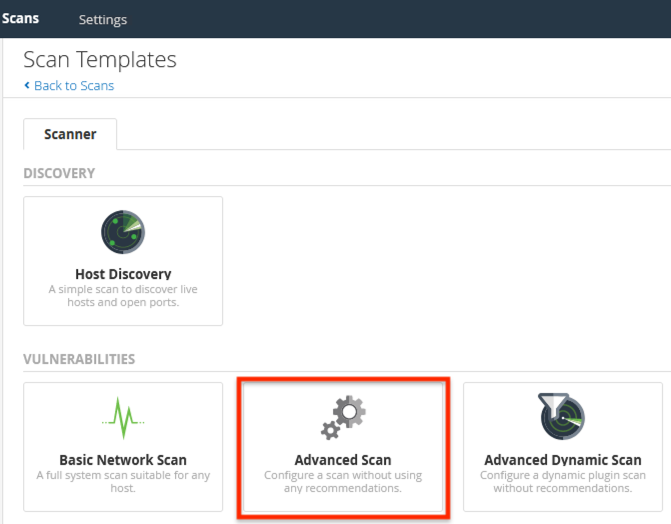
Scans can be initiated from the Scans tab then click on +New Scan

From the Scan templates Select scan template as per your requirement
Basic Network Scan or Advanced Scan
Enter Settings for the host to be scanned..like Name, Target(s)
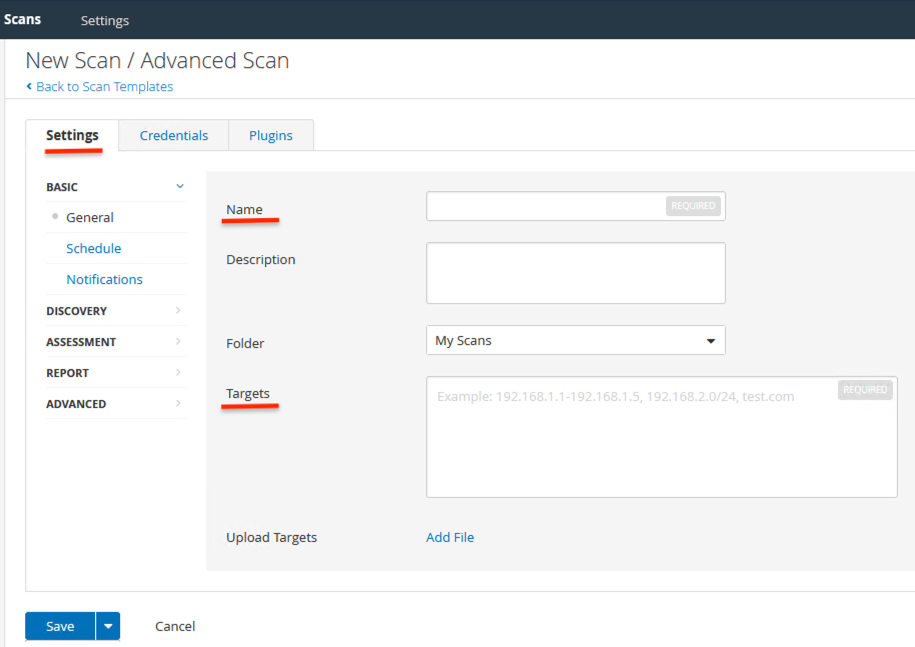
Enter Credentials – I have used SSH & Authentication method as password & entered the username & password of the Target to be scanned.
You can also consider using SOAP API credentials.
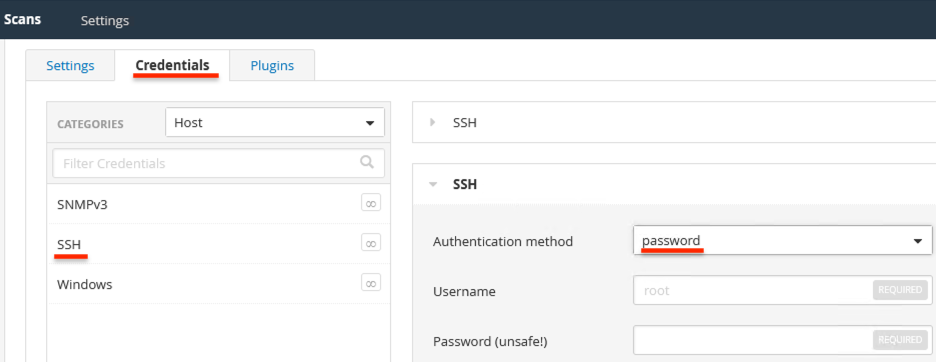
In Plugins tab all the Plugins are Enabled by default.
You can Enable/Disable them as per your requirement.
Click on Launch.
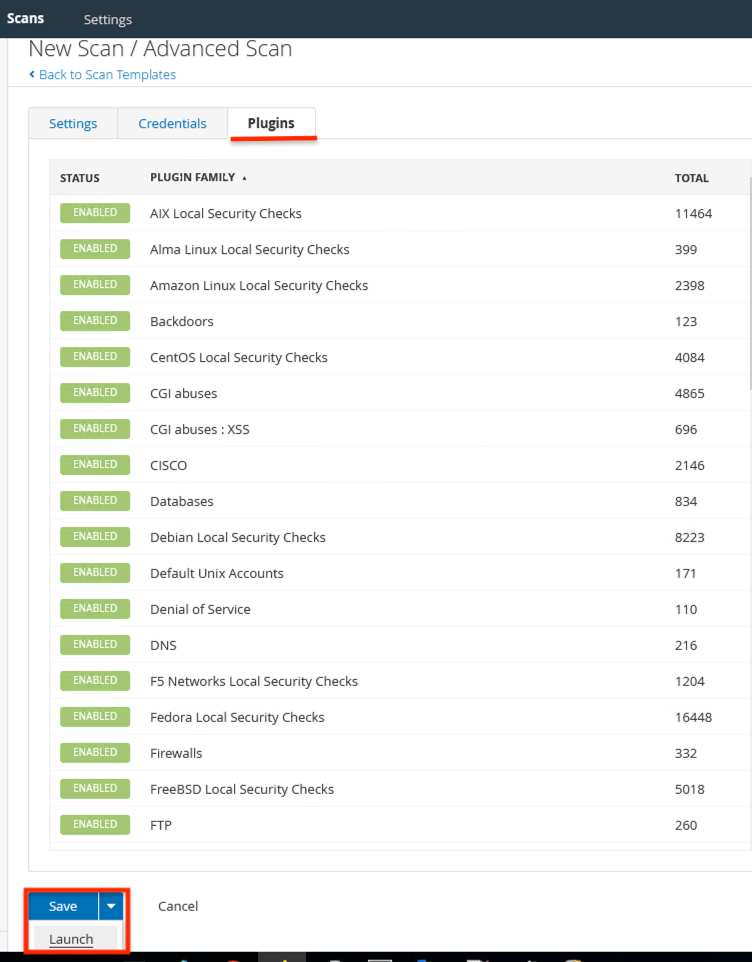
After scan is complete, the results can be seen by opening the scan results.
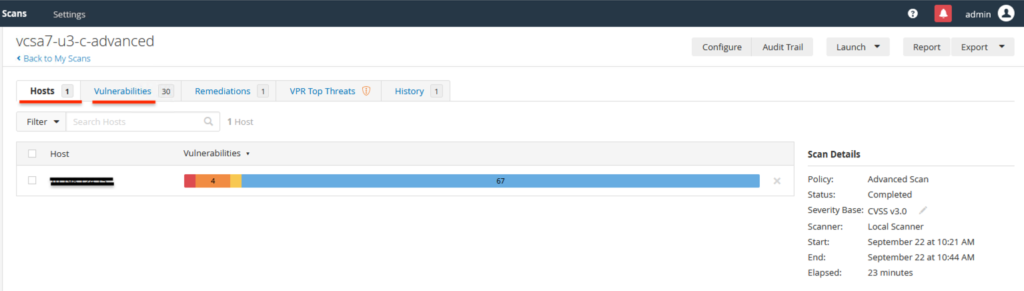
The vulnerabilities are classified as Critical, High, Medium, Low, Info.
You can click on each vulnerability to get more details about it & remediation details.
If you use Nessus Professional and above version then you can even find out the compliance related pointers.
I hope this data will help you secure your software stack.